Cybersecurity,
Redefined.
Protect your Company with our comprehensive platform.
We proactively detect security breaches and respond to cyber attacks to protect your technological infrastructure. Find out how!
Our comprehensively managed cybersecurity services
A comprehensive cybersecurity solution that provides real-time threat detection, analysis and response, creating a secure environment for your business.
Immediate assistance
Server and database protection
Operating system protection
Network protection
Account theft and payment fraud
DDoS and brute force attacks
Web Scraping and API Misuse
Vulnerability scanning
Automatic equipment evaluation
Real-time leak detection
Incident response plans
E-mail and phishing scams
It is well known that emails are often the initial point of engagement. For cybercriminals, it becomes a perfect attack vector that opens a gateway directly to your infrastructure. The biggest challenge is to automatically detect and block scams, phishing and malicious attachments while keeping your employees informed of mass and targeted attacks.
Online scams and phishing
As the most pervasive, behavioral and deceptive cyber threats, digital scams and phishing use an impressive array of techniques and tools. Phishing attacks are often disguised as online services, while phishing websites are hosted on compromised legitimate resources. In addition, more than half of high-tech crimes in 2021 were scams and phishing, making them one of the most challenging threats in history.
Lack of intelligence about scams
Fraudsters continue to innovate and change techniques, tools and schemes. It is a real challenge to keep up with them, and the only solution is to track, analyze and accumulate information about their activities because the efficient approach to fraud protection involves identifying networks of fraudulent resources and cybercriminal infrastructures on a daily basis.
Social engineering, vishing, scam calls
Protecting your customers from unsolicited phone calls, phishing scams or vishing becomes increasingly important as voice artificial intelligence technologies evolve.
E-mail and phishing scams
Online scams and phishing
Lack of intelligence about scams
Social engineering, vishing, scams
Account theft and payment fraud
DDoS and brute force attacks
Web Scraping and API Misuse
Vulnerability scanning
Immediate assistance
Server and database protection
Operating system protection
Network protection
Automatic equipment evaluation
Real-time leak detection
Incident response plans
Website rating
Every year there are 800,000 cyber-attacks. This equates to almost one cyberattack every 39 seconds.
HISCOX
44% of Spanish SMEs suffered at least one cyber-attack last year.
SOPHOS
Spanish companies spent $750,000 on average for ransomware attacks.
IT GOVERNANCE
96% of phishing attacks are sent via email.
Our products
A comprehensive cybersecurity solution that provides real-time threat detection, analysis and response, creating a secure environment for your business.
Scud Sensor
Find exposure in your network
A proactive cybersecurity tool that not only identifies vulnerabilities but also discovers assets and topologies, providing a holistic view of your network's security landscape.
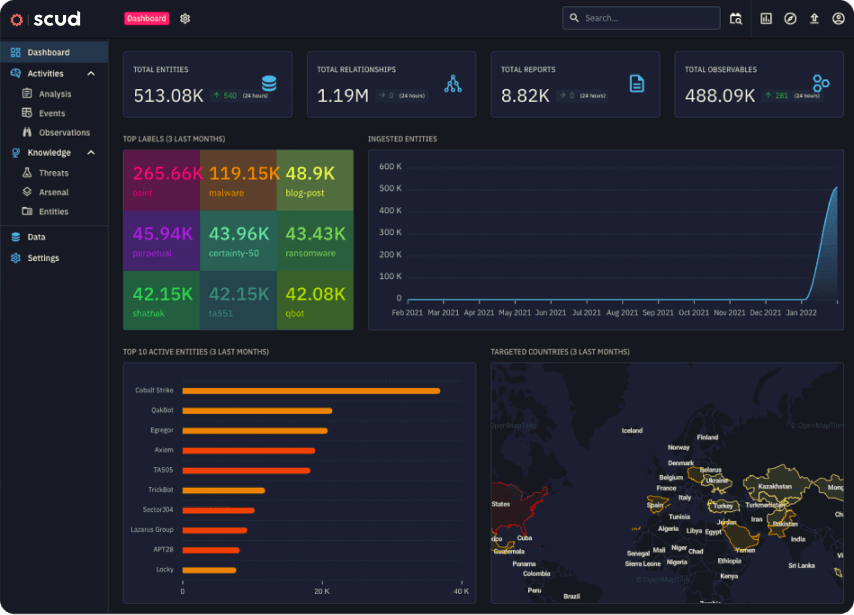
Scud Intelligence Platform
Managed detection and incident response
A comprehensive cybersecurity solution that provides real-time threat detection, analysis and response, creating a secure environment for your business.
Scud Monitor
24/7 continuous surveillance
An advanced monitoring solution that provides continuous surveillance of any parameter or information, ensuring up-to-date access.
How does it work?
Cloud-native detection and response supported by a team of cybersecurity experts 24/7.
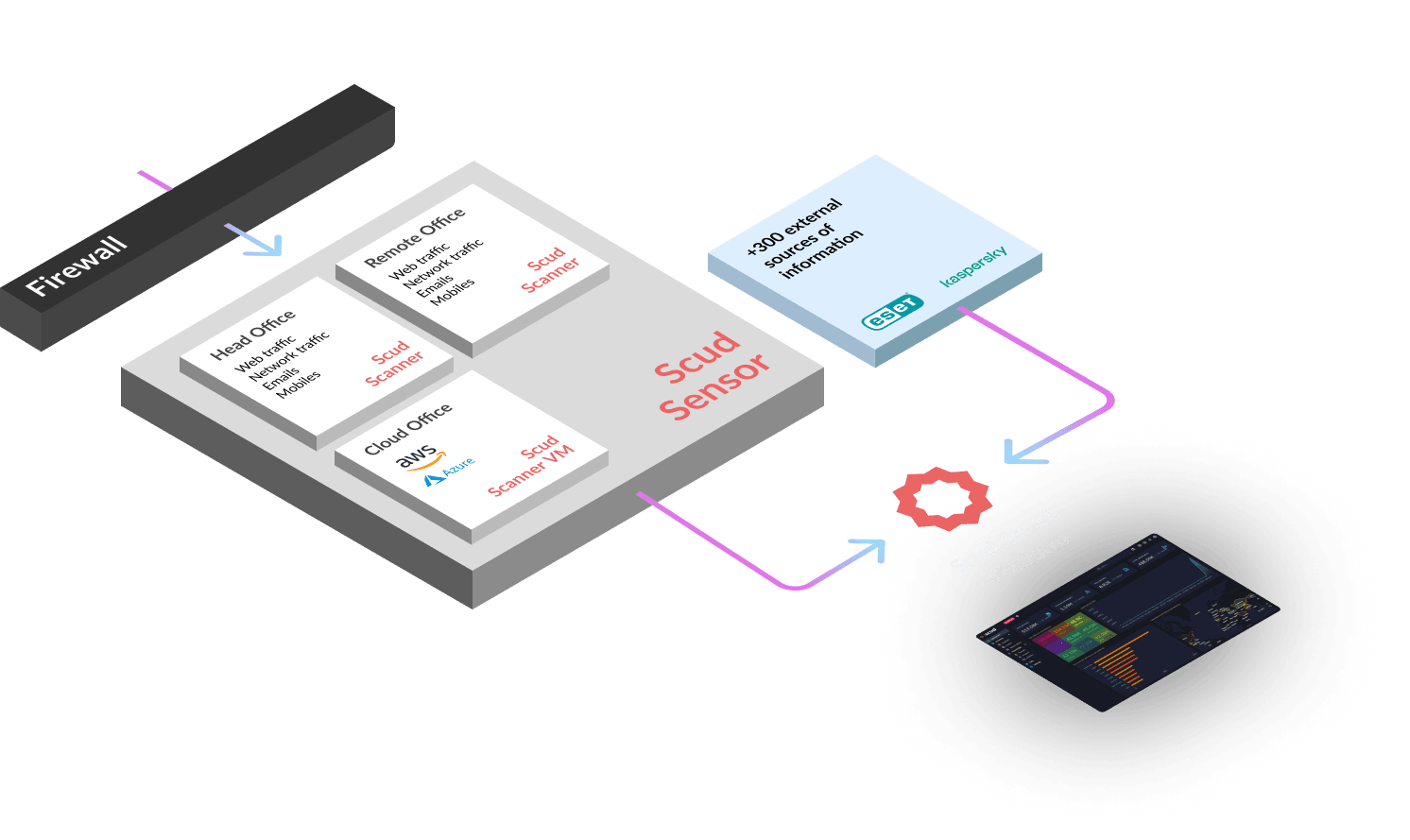
Scud Sensor VM
Analysis and discovery of active networks.
Vulnerability reporting (GVM, Tenable, Rapid7)
Asset and topology discovery
Can act offensively
Most of Sniffer functionality
Scud Sensor
Active network scanning and discovery.
Vulnerability reporting (GVM, Tenable, Rapid7)
Asset and topology discovery
Can act offensively
Most of Sniffer functionality
Scud Sniffer
Active network scanning and discovery.
Vulnerability reporting (GVM, Tenable, Rapid7)
Asset and topology discovery
Can act offensively
Most of Sniffer functionality
External data sources
Incorporation and correlation of any OSINT source.
STIX and TAXII streams.
Social Networks, RSS and other public feeds
API tracking of targets/topics
Files such as CSV, JSON, XML, TXT
Images
Vulnerability reporting (GVM, Tenable, Rapid7)
Asset and topology discovery
Can act offensively
Most of Sniffer functionality
Active network scanning and discovery.
Vulnerability reporting (GVM, Tenable, Rapid7)
Asset and topology discovery
Can act offensively
Most of Sniffer functionality
Active network scanning and discovery.
Vulnerability reporting (GVM, Tenable, Rapid7)
Asset and topology discovery
Can act offensively
Most of Sniffer functionality
Incorporation and correlation of any OSINT source.
STIX and TAXII streams.
Social Networks, RSS and other public feeds
API tracking of targets/topics
Files such as CSV, JSON, XML, TXT
Images
Why Scud?
We are not an end-point solution.
What sets us apart from other cybersecurity companies is our innovative approach to cybersecurity.
Our CDR (Continuous Defense and Response) service goes beyond the classic XDR services offered by other cybersecurity companies.
It is not only about protecting your network from external threats, but also about identifying and neutralizing threats that have already infiltrated your network and have gone unnoticed.
It is not an antivirus, we detect threats at the network level.
Our ability to monitor both your physical network and your cloud services gives us a bird’s eye view of your digital environment, allowing us to detect and respond to threats more effectively. With our CDR service, you get a level of protection that goes beyond what traditional XDR services can offer.
Inside and outside the network.
We understand that in today’s interconnected world, your network is not just limited to your physical facilities. That’s why our CDR service also extends to your cloud services, providing comprehensive protection regardless of where your data resides.
Sectors and Customers
We cannot give out the names of our customers.
We have strict confidentiality agreements and, above all, we do not want to give any advantage to potential attackers by revealing details of our customers’ technological structure.
But we can give some examples of sectors and company sizes where Scud technology has been in use for years
Airlines
Scud is installed in an Asian airline with a turnover of more than $2 billion in 2023.
Automotive
Japanese automotive company with more than 2.8 billion in turnover uses Scud technology
Logistics
A German company with a turnover of more than 6,000M Euros and 30,000 employees enjoys the security that Scud provides in all its operations.
Electricity
A medium-sized electricity trader with a turnover in excess of €50M has managed to stop several attacks thanks to the advanced technology provided by Scud.
SMEs
Scud technology is the same for both large and small and medium-sized companies.
The only difference is the number of Scud devices installed and the size of the supervisory team.
Electronics
In Asia, an electronics giant uses Scud sensors and software in one of its divisions (with a turnover in excess of €6 billion).
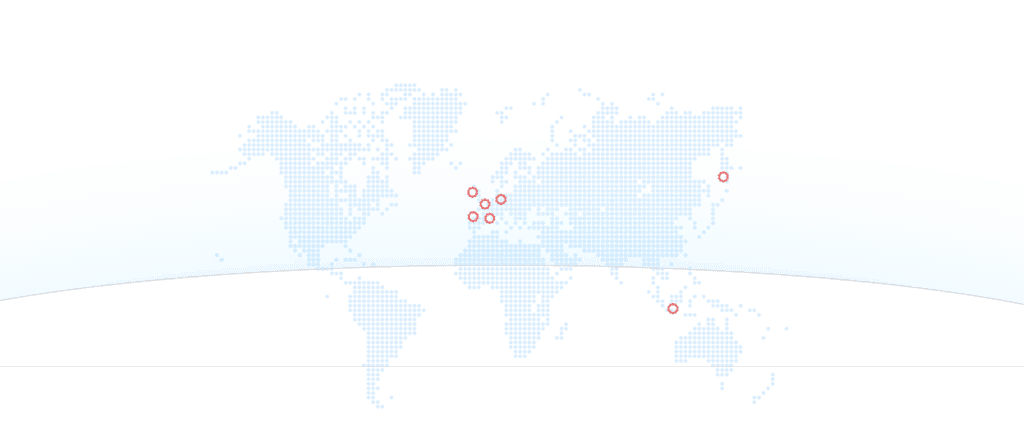
Scud in the world
Our company prides itself on its extensive network of partner companies spanning Germany, the UK, Malaysia and the US. This international alliance brings together more than 200 interconnected professionals, providing us with a wealth of cyber-attack information from a wide range of sources.
Our company prides itself on its extensive network of partner companies spanning Germany, the UK, Malaysia and the USA.
This international alliance brings together more than 200 interconnected professionals, providing us with a wealth of information on cyber-attacks from a wide range of sources.
Have you been hacked? Call us.
When a cyberattack occurs, every second counts. That’s where our Cyber Emergency Response Service (CERS) comes in.
Our team of cybersecurity experts is ready to spring into action the moment you've been hacked, helping you mitigate the damage, protect your network and restore normal operations as quickly as possible.
Once the immediate threat is neutralized, we will work with you to investigate the incident, identify how the attackers breached your defenses and strengthen your security to prevent future attacks.
With CERS, you're never alone in the face of a cyberattack.
Want to see Scud
Intelligence Platform in action?
Request a demo and see firsthand how Scud is not your traditional cybersecurity software.
Discover how our products and services can provide you with the robust, comprehensive and easy-to-use security you need.
Simply fill out the form and one of our solutions consultants will contact you to set up an appointment to show you how it works.